Hackers targeting a specific exploit that involves Office and Windows products, warns Microsoft. Today’s “Patch Tuesday” was accompanied by a report that malicious Word documents were being distributed over email. The exploit allows hackers to “gain the same user rights as the logged on user” by corrupting system memory, which allows attackers to execute arbitrary code.
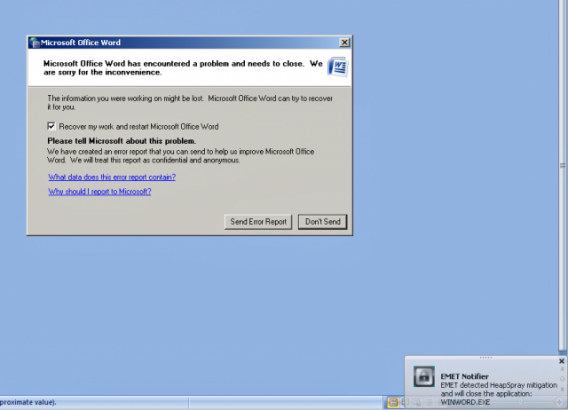

Microsoft has not released a patch to fix this but does advise users to download a temporary workaround in the mean time. The attacks focus around exploiting graphics images embedded into a Word document. The temporary workaround merely blocks that type of graphic from being displayed at all, making rendering the exploit useless but also disrupting the user experience since they won’t be able to load that type of graphic.
The exploit affects Windows Vista and Windows Server 2008, Microsoft Office 2003 through 2010, and all versions of Microsoft Lync. The way Office 2010 renders graphics makes it only vulnerable when running on Windows XP and Windows Server 2003. The exploit won’t work on Office 2010 if run in Windows 7, 8, or 8.1. In fact, Windows 7, 8, and 8.1 aren’t affected by this exploit at all.
This type of attack is extremely targeted and most users won’t have to worry. Still, those who want to protect themselves from any possibility of this attack should install the temporary workaround while Microsoft patches Office and Windows.
UPDATE 11/7/13: Microsoft has released another blog post clarifying which Office and Windows products are affected by this exploit. The attack is targeted toward Office 2003 and 2007 users, regardless of which version of Windows they’re installed on. Office 2010, on the other hand, can only be exploited on Windows XP or Windows Server 2003. For more info about this exploit, check out Microsoft’s blog post.
RELATED STORIES
- LinkedIn Intro called “a dream for attackers” by security researchers
- New versions of Chrome will lock saved passwords
- Firefox to mark all Java versions as unsafe
Source: Microsoft | Ars Technica

